🔐Security considerations
Security Considerations
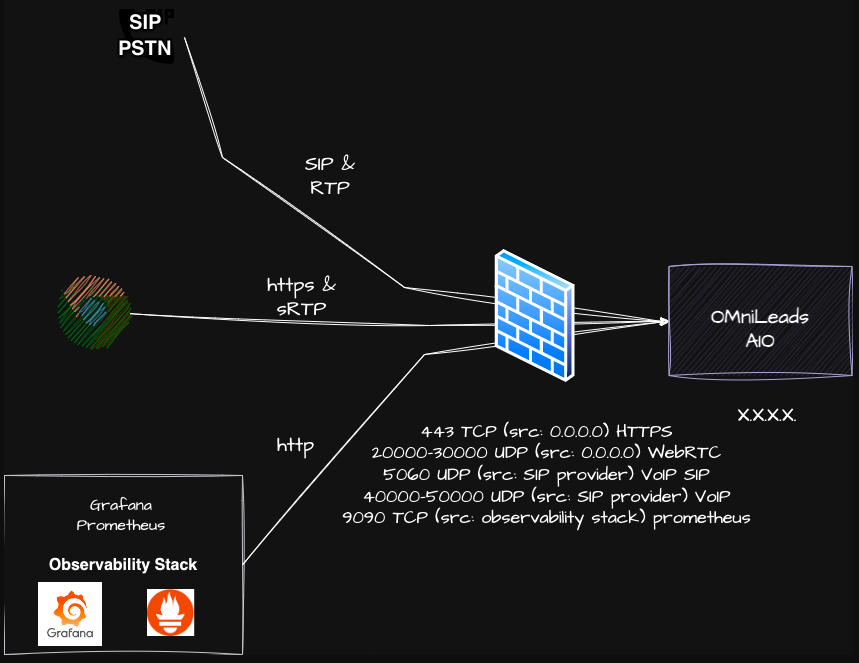
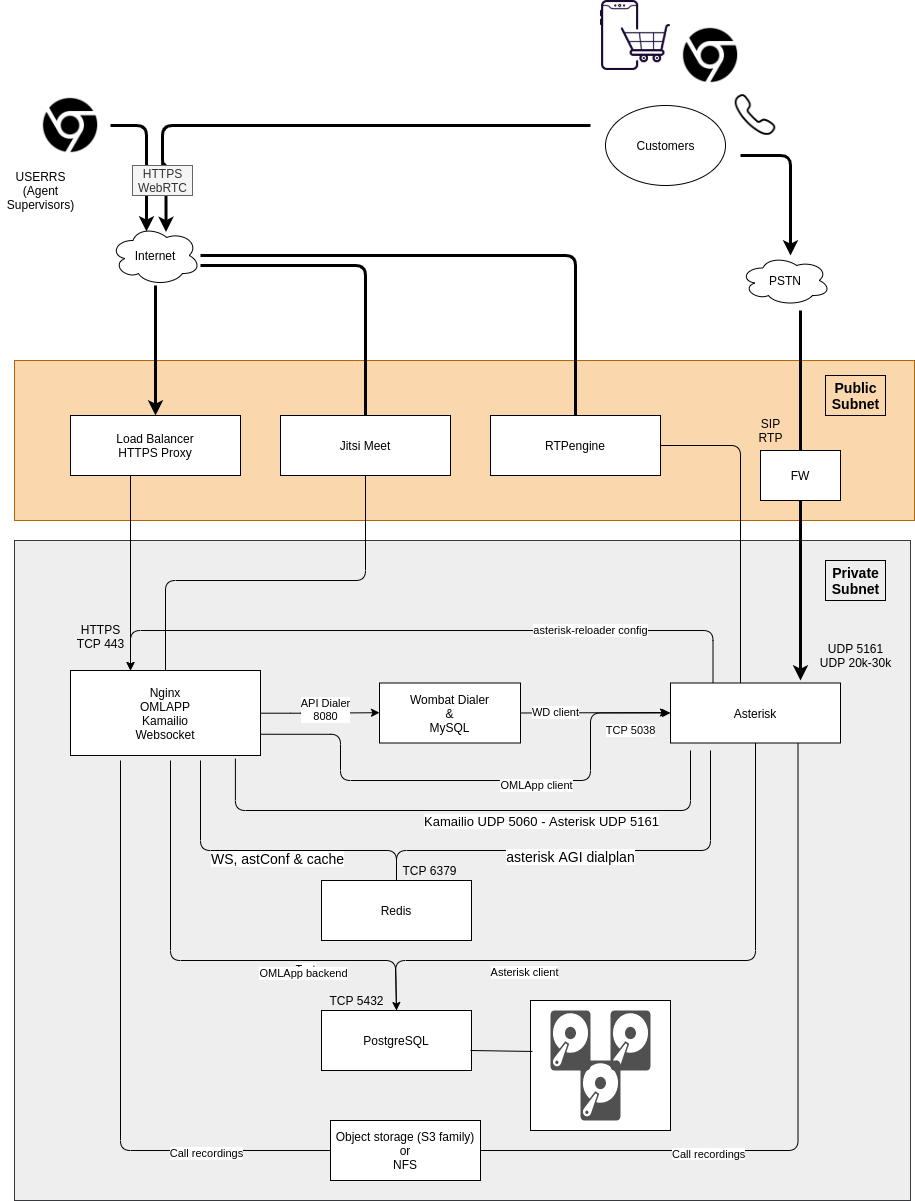
OMniLeads is a web application, designed to operate under the protection of at least one perimeter firewall or cloud firewall in a cloud computing environment.
Ideally, it is recommended to deploy OMniLeads together with an HTTP Proxy or Cloud Load Balancer for HTTPS requests and a Session Border Controller for VoIP edge management.
This greatly strengthens the security of your deployment. Considering the scenario where users will access the application both from the local network and from the Internet, the following list of ports must be exposed to the outside:
UDP 5060: SIP traffic coming from the PSTN. Must be validated by source IP (src: SIP Provider).
UDP 40000 a 50000: RTP/UDP traffic coming from the PSTN. Must be validated by source IP (src: SIP Provider).
UDP 20000 a 30000: WebRTC traffic coming from users. In this case, users are assumed to be in home-office mode, so it is left open to the Internet (src: 0.0.0.0).
HTTPS 443: Web and WebRTC traffic from users. In this case, users are assumed to be in home-office mode, so it is left open to the Internet (src: 0.0.0.0).
TCP 9090: TCP traffic coming from the Prometheus component of the Observability Stack (src: Observability Stack).
All in One type deployment:
Cluster deployment on a cloud-computing scheme:
Important!
In case you need to expose VoIP ports to the ENTIRE Internet, it is recommended to manage VoIP security using a Session Border Controller or an Asterisk or Freeswitch configured as a SIP border component, so that OMniLeads is not exposed to all IP addresses. At the very least, you will start receiving SIP junk from multiple sources.
Last updated