External Authentication
External Authentication Configuration
To configure External Authentication based on LDAP, the administrator must go to the Security Menu → Authentication and configure the options corresponding to their environment: Microsoft Active Directory or OpenLDAP. This authentication method allows the platform to authenticate each user access through an external LDAP service (Lightweight Directory Access Protocol). For operations that require user authentication through External Systems, OmniLeads adds Authentication via protocol starting from Official Release 1.32.
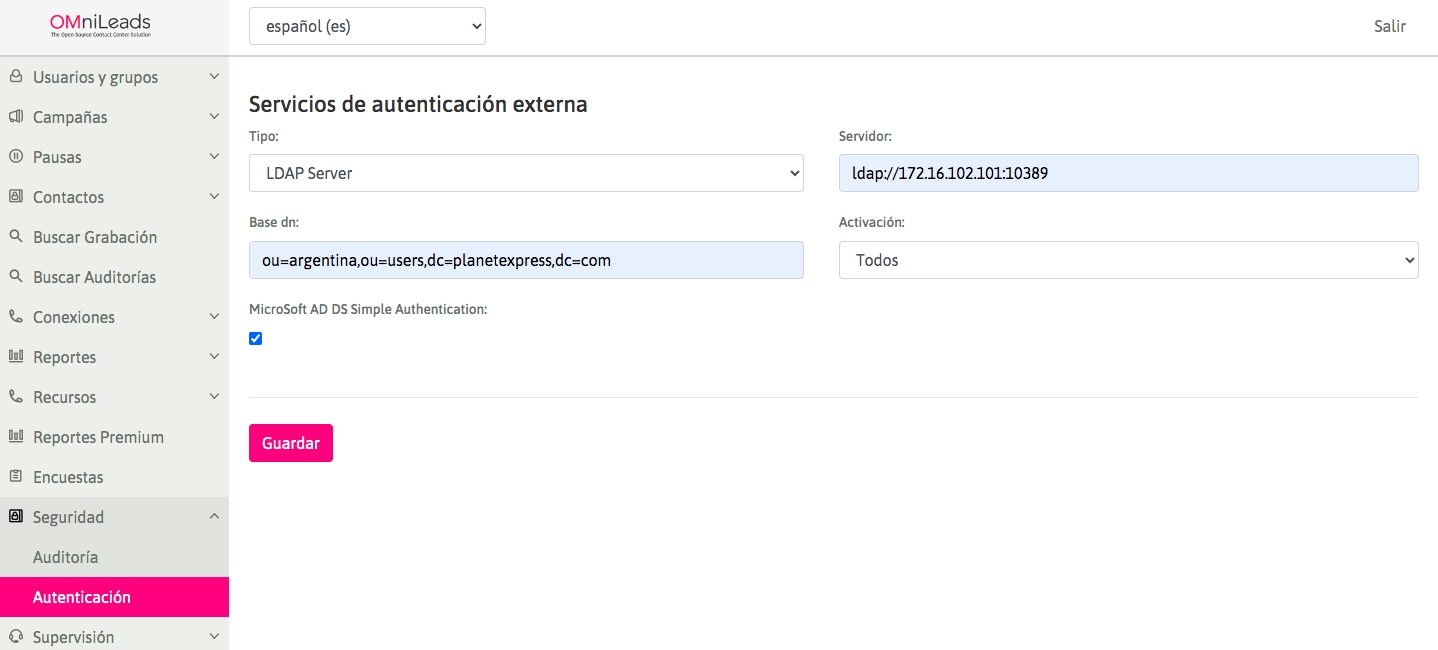
Check Simple Authentication AD: This checkbox uses username formats like user@domain when joining services based on Microsoft Active Directory LDAP.
Activation: Option to activate the feature.
Base DN: Distinguished Name describes the base path in the info tree that will guide the protocol to the desired search result.
Server: The URI for server contact, prepending protocol and specifying IP address or FQDN (full hostname) and port, as shown in the image.
Type: Select LDAP (in future releases, other external authentication mechanisms will be added).
In the example, “172.16.102.101” refers to the Network Address of the server where the external authentication Backend (OpenLdap or Microsoft Active Directory) is hosted. In turn, “:10389” indicates the port where said service is exposed.
On the other hand, the BaseDN field refers to the “Distinguished Name” that will be used as a basis to quickly explore the DIT (Directory Information Tree) and find the search result.
In the example, the string “dc=planetexpress, dc=com” comprises DC (domain accessor) fields used by the Domain Name System (DNS) mapping. However, this field can be as extensive as required, such as Company Name (O), Organizational Units (OU) and/or Common Name (cn) for user groups.
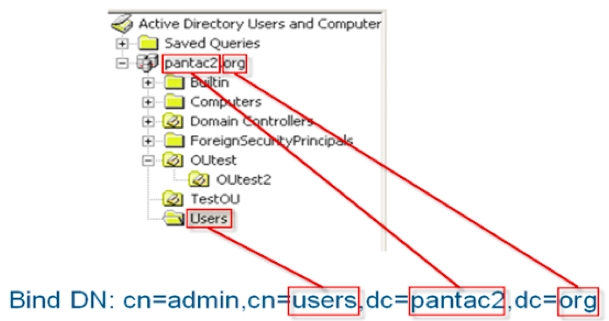
Below is an example based on Microsoft Active Directory. If a user account is in the Users ldap container or resource, the Base DN binding information would look like this: “cn=users,dc=pantac2,dc=org”. In this case, by activating the Simple Authentication checkbox previously described, the credentials transmitted to Active Directory are expressed in the username@domain format, where "domain" is replaced by the domain access fields -DC- ([email protected], in the example).
Activation Methods
When activating authentication via the LDAP protocol, the activation mechanisms can be:
Manual (default inactive): Each new user will inherit the "Legacy" authentication when registered in the system. However, the administrator can modify the user's configuration at any time.
Manual (default active): Each new user will forcibly inherit external authentication when registered in the system. However, the administrator can modify the user's configuration at any time.
All except Admin: All users will be configured with external authentication by default, except the system's Admin user.
All: All users will be configured with external authentication by default.
To verify the user authentication settings, simply go to the Users view in the system and check the Authentication column, as shown in the following image:
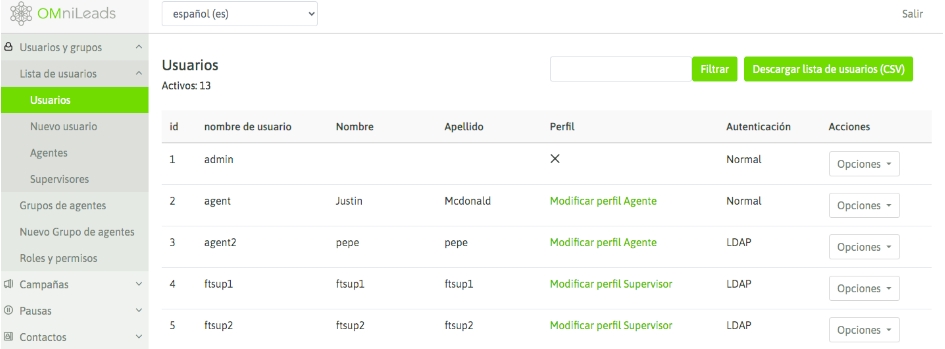
External authentication can be enabled in the user view as long as an external authentication service is configured in the Security menu of the system, as explained in the previous section.
Additionally, to create new users or edit existing ones, the administrator can modify their access method through the user's detailed view.
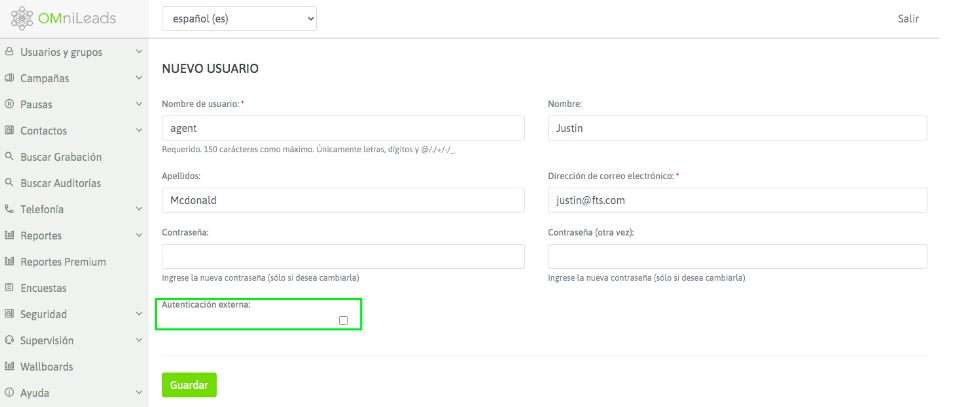
LDAP Authentication services:
If External System Authentication is enabled for a user and they log in to the system, OMniLeads will use the said External Authentication Backend to access.
IMPORTANT: Since OMniLeads delegates authentication to another entity, it is crucial that the user is created in the external directory system to ensure consistent authentication.
If the authentication process is not successful, the user will receive an access error message; otherwise, they will be able to use the platform normally.
If the LDAP service is down and the Admin user also uses LDAP for access, there will be a chance to recover access to the system through a command executed by the root user of the Operating System (superuser):
source /opt/omnileads/virtualenv/bin/activate
cd /opt/omnileads/ominicontacto
python3 manage.py desactivar_autenticacion_externa
Last updated